Using Secretless in Kubernetes
Estimated time to complete: 5 min
Products used: Kubernetes Secrets, PostgreSQL Service Connector
Overview
Applications and application developers should be incapable of leaking secrets.
To achieve that goal, you’ll play two roles in this tutorial:
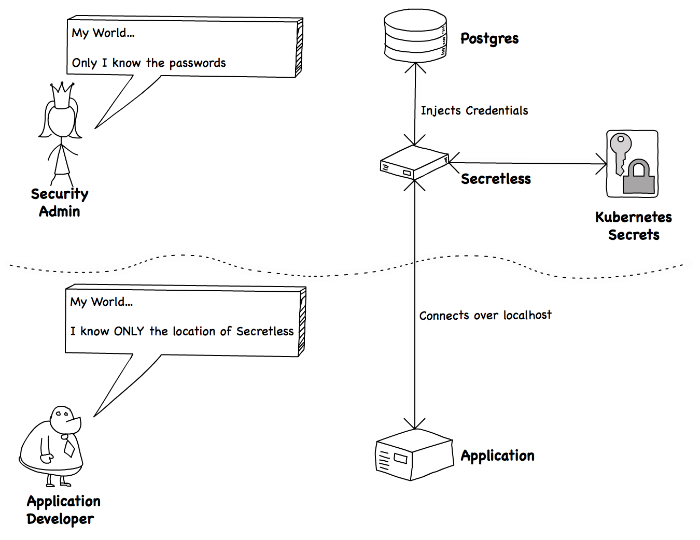
- A Security Admin who handles secrets, and has sole access to those secrets
- An Application Developer with no access to secrets.
The situation looks like this:
Specifically, we will:
As the security admin:
- Create a PostgreSQL database
- Create a DB user for the application
- Add that user’s credentials to Kubernetes Secrets
- Configure Secretless to connect to PostgreSQL using those credentials
As the application developer:
- Configure the application to connect to PostgreSQL via Secretless
- Deploy the application and the Secretless sidecar
Prerequisites
To run through this tutorial, you will need:
- A running Kubernetes cluster (you can use minikube to run a cluster locally)
- kubectl configured to point to the cluster
- Docker CLI
Up next...
Play the role of a Security Admin and learn how to set up PostgreSQL and configure Secretless.